
Mobile Workforce Secure Cloud Access
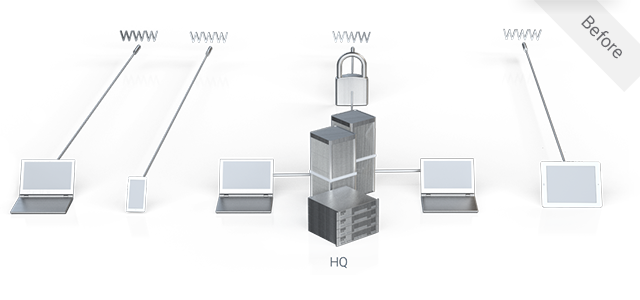
No Visibility and Control for Mobile Access to the Cloud?
Mobile users, especially those using personal devices for work, can connect directly to the cloud, which bypasses corporate network security policies. Alternatively, forcing users through a specific network location, such as a datacenter firewall, impacts performance and the user experience – often leading to non-compliance.
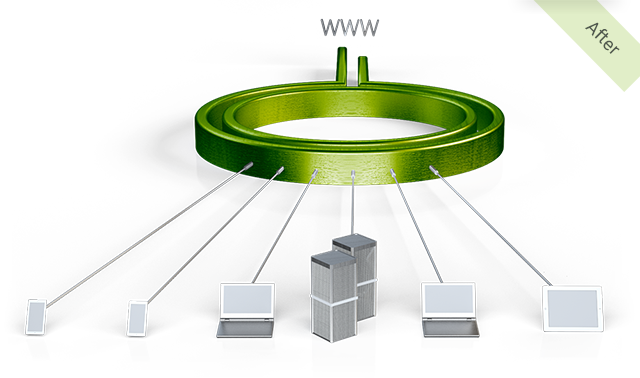
Secure and Optimize Mobile Cloud Access, Everywhere
Cato connects every mobile user to the Cato Cloud and provides secure and optimized access to enterprise resources in physical and cloud datacenters, cloud applications and internet sites. With compatible cloud applications, it is possible to restrict access to the Cato Cloud IP range, so stolen credentials cannot be used to access enterprise data in the cloud.
Optimal Connection at Every Location
Each device connects to the nearest Cato Cloud Network PoP to ensure optimal access to every resource regardless of the user’s location. Cloud applications can be configured to accept traffic only from the Cato Cloud Network to ensure compliance.
Extend Security Policy to the Mobile Workforce
All mobile access is protected against malicious web sites. Corporate security policies are seamlessly extended to control mobile access to sensitive data, both on-premise and in the cloud.
Fast, Self-Service End User Deployment
Quickly onboard users into the Cato Cloud Network. End users are invited to a guided, self-service deployment of the Cato Client for laptops, smartphones and tablets, including BYOD devices.
