
Cato Cloud
Software-defined and Cloud-based Secure Enterprise Network

Call a Specialist Today! 833-335-0426


Cato Editions address diverse enterprise needs and deployment scenarios
Cloud and Internet traffic is carried over multiple links to the Cato Cloud and secured by Cato Security Services.
WAN traffic is handled by current WAN.
WAN and Cloud traffic is carried over an optimized overlay of Internet links to Cato, or using MPLS links.
Cato Security Services secure all traffic.
WAN and Cloud traffic is carried over an optimized overlay of Internet links to Cato, or using MPLS links.
Security is handled by existing network security stack.
Request a Demo! View Demo Video!
No more appliance sprawl and managing multiple point solutions. Cato connects your business into one global network, secured by enterprise grade security services, enforcing a unified policy and managed via a cloud-based management application.

Avoid expensive backhauling over MPLS or using high latency internet links. Using Cato’s optimized Cloud Network, customers will enjoy tightly-managed, SLA-backed, global backbone at an affordable price.

Cato’s global Network and Security Operations Center, manned by network and security experts, augment your IT teams with crucial network management and network security skills to ensure your business remains connected and secured 24/7/365.

No need to settle for dumbed-down, capacity constrained, UTM appliances. Since Cato is built upon elastic cloud infrastructure, your business is protected by enterprise-grade security that seamlessly scales to meet your needs.

With full visibility of the traffic flowing through the Cato Cloud, Cato Research Labs can identify emerging threats at any given customer and proactively deploy countermeasures to protect all customers.

Skip those tedious updates and upgrades of appliances and their software. Cato agile cloud software is constantly and seamlessly updated to incorporate the most up-to-date defense against emerging threats.
A global, optimized and secure enterprise network backbone
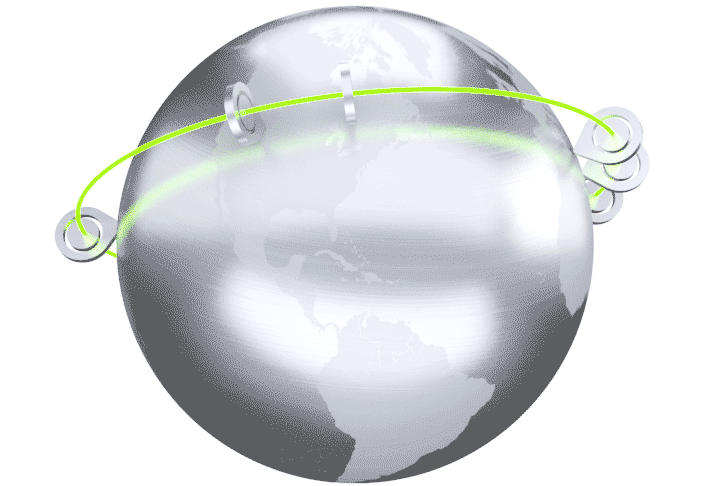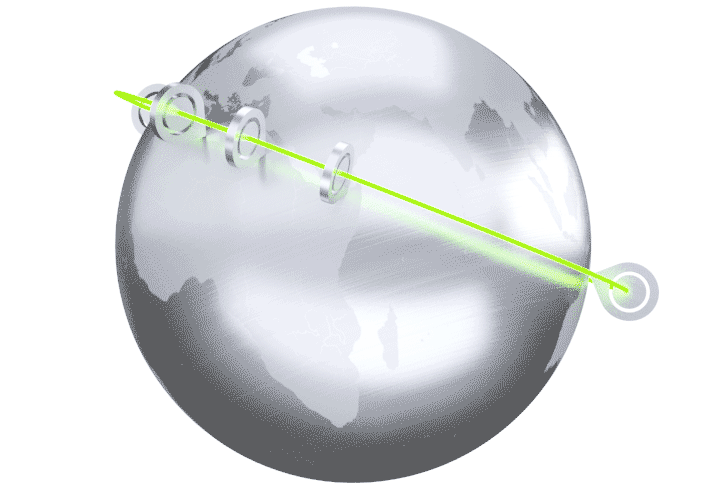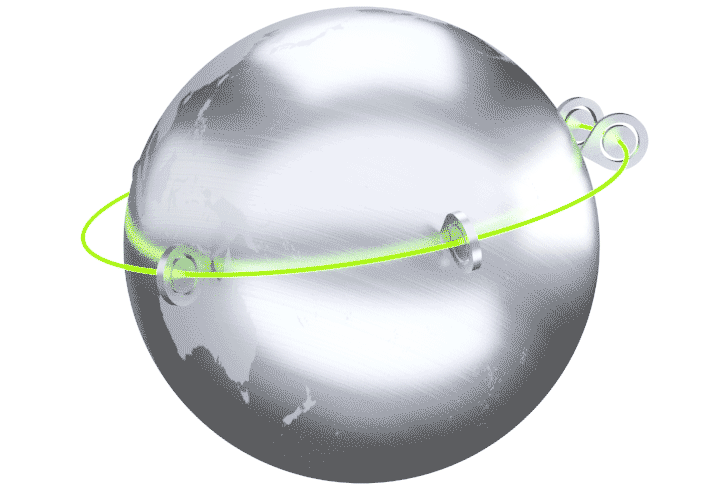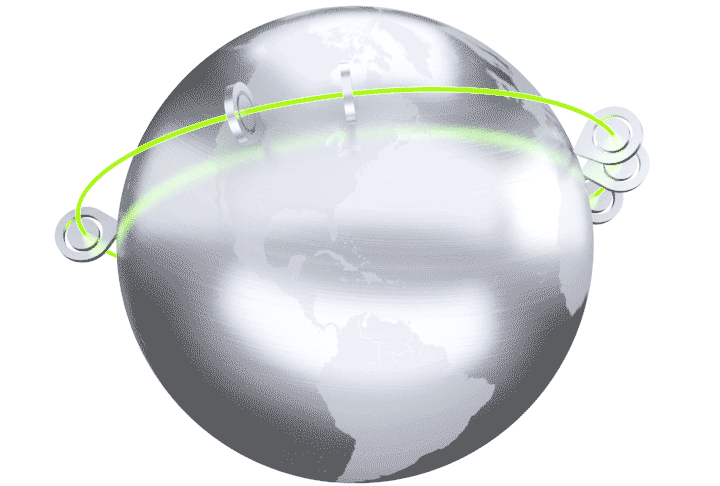
The Cato Cloud Network is built on a globally distributed network of Points of Presence (PoPs). The PoPs are interconnected with an encrypted and optimized multi-carrier private backbone to ensure optimal global traffic routing. The Cato Cloud Network provides an affordable, SLA-backed, global enterprise network backbone.
Cato holistically connects all network elements including branches, mobile users, physical and cloud datacenters. Connectivity is dynamically established to the nearest PoP so “last mile” latency is minimized. Regardless of physical PoP connection, Cato creates a single logical abstraction of the enterprise network with full visibility and control of all network traffic.

Admins can configure existing network and security equipment (routers / firewalls) to securely tunnel traffic to the Cato Cloud.
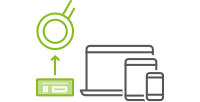
Cato provides multiple secure tunnelling solutions to the Cato Cloud Network. The Cato Socket is a zero touch appliance for physical locations. The Cato vSocket is a virtual socket for cloud datacenters. The Cato Client is a software client for laptops, tablets and mobile devices.
View Demo Video!
Subscribers of Cato’s partner ISPs enjoy seamless tunnelling of their traffic to the Cato Cloud.
Enterprise grade, elastic and agile network security services, tightly integrated into the Cloud network.

Cato security services are deployed at each PoP and enforce the organization’s security policies on all traffic, including internal traffic between network participants and traffic going to and from the Internet.
Without the constraints of physical appliances, Cato security services can scale to support business growth. Additionally, Cato experts seamlessly update the Cloud-based software to address emerging threats.
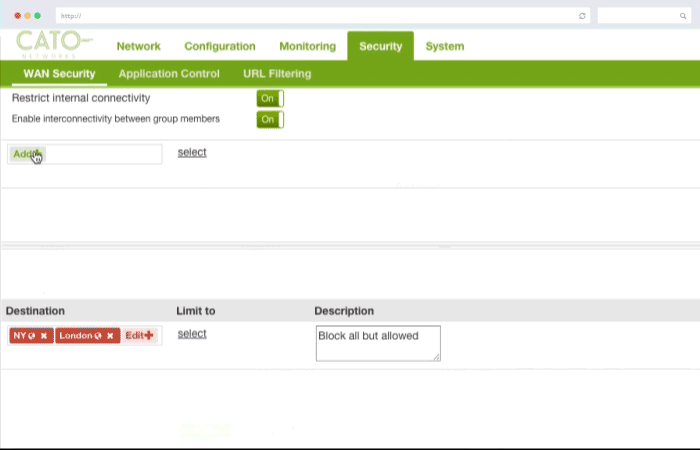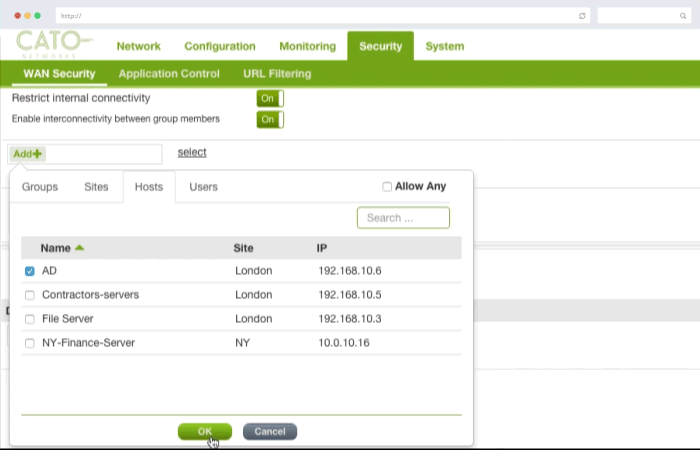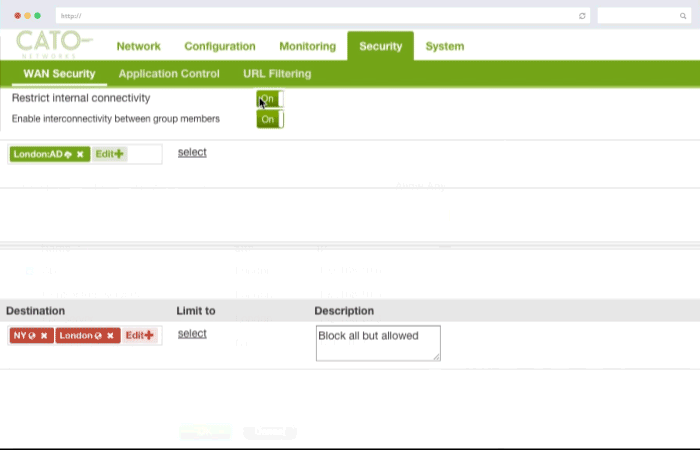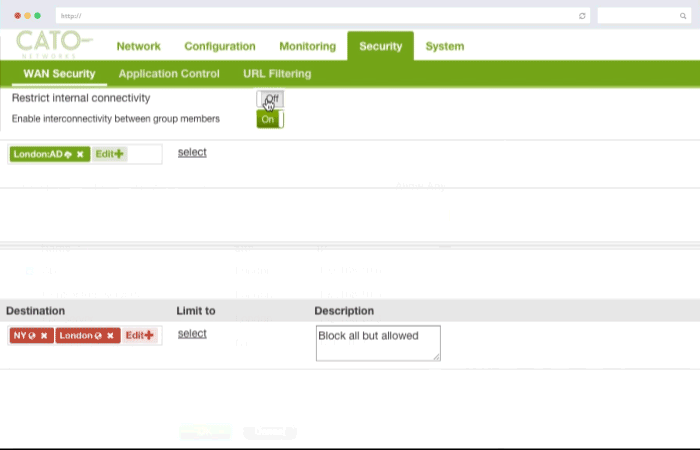
Security policies can be applied corporate wide or down to specific users and locations to secure access to both on premise application instances as well as Cloud applications such as Salesforce and Dropbox.

Protects internet, cloud and WAN traffic at any location using application aware policies, without hardware appliances or traffic backhaul. Seamlessly scales to support multi-gigabit traffic and upgrades with new capabilities and countermeasures against emerging threats.

Detects and prevent access to phishing and malicious websites to minimize the risk of credential theft, vulnerability exploitation, and malware infection.

Inspects all traffic for a wide range of threats using multiple layers of protection to prevent compromise of users’ desktops, laptops, tablets, and smartphones.

Controls and secures access from mobile devices to cloud applications (Office 365, Salesforce, etc.) and cloud infrastructure (Amazon AWS, Microsoft Azure).
View Demo Video!
Consolidates network and security events for analysis by Cato’s Management Application or sharing with third party tools such as SIEM. Cato Research Labs performs ongoing evaluation of network activity for malicious traffic within the corporate network and to the Internet.

Provides in depth visibility into overall network activity by location, applications, groups and users. Admins can centrally configure application-aware policies to control resource usage and access, and be alerted to security and network events.
Cato Networks Management Application
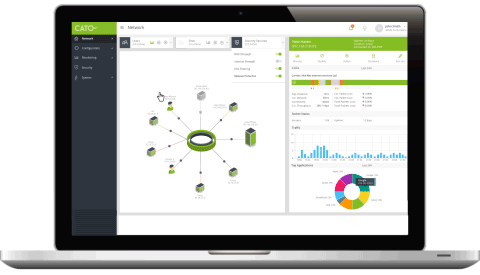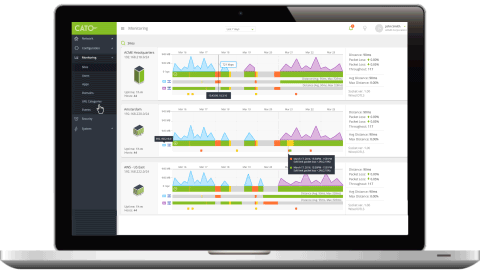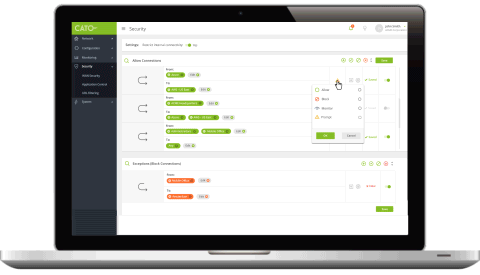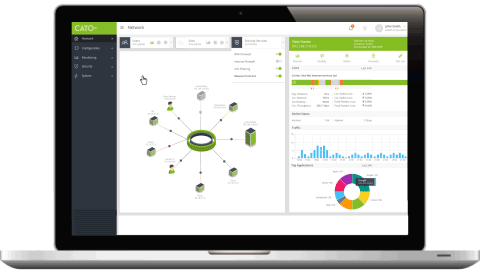
Cato Management Application enables full traffic visibility for the entire organizational network and a way to manage a unified policy across all users, locations, data and applications (both internal and Internet/Cloud-based).
The Cato Cloud environment is managed by Cato’s global Network and Security Operations Center, manned by a team of network and security experts to ensure maximum uptime, optimal performance and highest level of security.

Cato Cloud Solution Brief (.PDF)